CryptoLocker Removal Tool: Decrypt CryptoLocker Virus Files for Free!
CryptoLocker Decryptor & Removal Tool Guide
The internet has always been the mix of good and evil. Of course, you can do tons of useful tasks using the web. On the other hand, there are many hidden snares to trap you as well.
Relatively new to this range of online threats is ransomware. Most of you are hearing this name for the first time. In this article, you are going to read about a special type of ransomware. Hence, it is important for you to know what it is.
Simply put, a ransomware is a type of virus. On contrary to the functioning of ordinary malicious programs, a ransomware either locks files or restrict the access to them and demand some monetary amount (ransom) to revoke the affected state. In case you don’t give them money (mostly in the form of bitcoins), you will lose the files forever. It’s not just the PC users but Netflix users are also in trouble with the latest ransomware.
I hope you got a brief idea about ransomware now. Let’s move on to CryptoLocker.
What is CryptoLocker Ransomware/Virus?
As I said earlier, CryptoLocker is a type of ransomware that demands money to revoke file access.
Once CrptoLocker gets into your system, it scans for different types to encrypt them. For each file it encrypts, it generates a random key and locks the content using AES algorithm. Then, it makes everything complicated by encrypting that random key with RSA algorithm and finally, the main key is added to the encrypted file.
The effective way to crack such a code is bruteforce attack. But it will take more than thousand years for a personal computer to get the correct key through this attack.
Only the owner of KryptoLocker gets the random key for decryption. Even a computer forensic expert can’t figure out the key because the data on the system is regularly overwritten. Now you know what a CryptoLocker virus is, right? Let’s move on to the next section then.

How Does CryptoLocker Virus Get into my System?
There may be many methods through which CryptoLocker ransomware gets into a computer. But the most seen method is the one given below.
As in the case of many malicious programs, the most possible way for the CryptoLocker virus to get into your system is emails. Yeah, you read it right!
You will get see-to-be genuine mail from a logistics company. There would be a zipped file as an attachment. In order to increase the credibility, the file has a password, which you can get from the mail itself.
Once you open the zipped file, you will see a harmless file like PDF or JPG. Truth be told; the real executable extension (.exe) will be hidden. As you open the file, CryptoLocker permanently stick to your computer and starts working.
How Does CryptoLocker Virus Work?
Now that you know what CryptoLocker is and how it gets into your computer, I want you to have an idea of its working as well.
When you open the PDF or JPG file from the zipped archive, CryptoLocker does three things on your computer.
- Triggers two CryptoLocker processes. One is the main one and second makes sure the primary program doesn’t get terminated.
- Adds a registry key to ensure the ransomware is started every time you boot up your computer.
- Stores the pivotal files to a folder inside user.
For the first time, it scans your computer for the specific types of files (included in the algorithm of the ransomware). It follows the above given method to encrypt each file. Due to the double encryption, cracking the key becomes impossible.
The registry key it creates is HKCUSoftwareCryptoLockerPublic. Moreover, it creates another registry key to log the details of the encrypting files. Such details are logged into HKEY_CURRENT_USERSoftwareCryptoLockerFiles.
Once the program finishes scanning your entire system for the files, it will show a wizard with a countdown. Usually, you will get about three days of time to pay the requested amount in the form of bitcoins. In the wizard, you can also read that the private key needed for decryption gets destroyed soon after you try to remove or damage the CryptoLocker ransomware program.
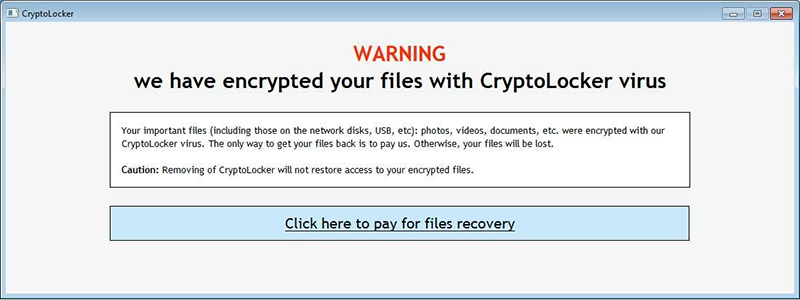
Types of Files Affected by CryptoLocker Ransomware
As I said earlier, CryptoLocker doesn’t lock every single file on your computer. The developer of the ransomware should have specified the file types. The common types of files that can be affected by CryptoLocker are given below.
“ .sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt”
I know these are a lot. And, I hope you got the idea of the range of CryptoLocker virus now The files encrypted by Cerber ransomware are almost similar to CryptoLocker virus.
CryptoLocker Removal Tool & Guide
Considering the risk level of the CryptoLocker ransomware, I don’t think there is a single tool that can get rid of it from the root. Here I use a combination of a couple of antimalware tools to remove it.
Step 1: First, you have to log into safe mode with networking. Doing the same in earlier versions of Windows (XP, Vista and 7) is easy. Restart your computer and while it boots up, you have to press F8 (F10 for some systems) to get a CMD-like window. Choose Safe Mode with Networking from there.
If you are a Windows 8, 8.1 or 10 user, you have to hit Win key+ R. Then, enter msconfig into the field and press Enter. On the new wizard, access Boot tab. Under boot options, check Safe mode and turn on Network. Finally, restart your computer.
Step 2: Once the system starts up, you have to download and install a program called RogueKiller. You must know the architecture of the OS (x32 or x64). Then, download the right one.
Don’t forget to proceed to the installation just like you do for any other software as well. (I hope you don’t need a guide for installation provided there is nothing complicated in it).
Step 3: Open the software after finishing the installation. As you are running it for the first time, you will see it prescanning. Wait some time to get it completed.
Then, click on Scan to kick-start the analysis for malicious files.
Step 4: When it is completed, you have select and hit Delete to remove them.
Not a single antimalware tool is perfect. For the same reason, I want you to install another desktop app as well.
Step 5: Download the executable file and install Malwarebytes Antimalware software.
Step 6: Open the software after you complete the installation. Then, choose Quick Scan and hit Scan button to start scanning for malicious files.
Step 7: When the window finishes the scanning, you have to hit Ok once and on the following screen, you should click on Show results.
Step 8: At this step, you will get the details of all the infected files. Just select all the files and, click Remove selected. There you go.
Step 9: Finally, you have to press Yes to restart your computer to see the malware removal in effect.
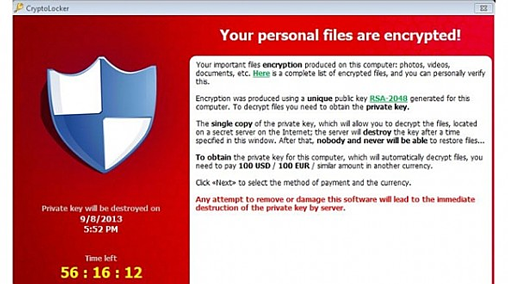
How to Decrypt CryptoLocker Infected Files
In the above section, you read how to remove CryptoLocker. Here you will get to know how to restore the infected files.
Step 1: The software we use here is ShadowExplorer. Obviously, you have to download and install this. (There is a portable version available to be used just in case you blocked from installing anything).
Step 2: Open the software after installing or downloading the portable version. First, you have to choose the drive in which the folder/file you want is present.
The next dropdown menu is used to choose the date. You should choose a date prior to that of CryptoLocker infection.
Step 3: Now you have to choose the exact folder or file from the main window on the right side.
Then right- click on it and choose Export.
Step 4: Finally, it will ask you for a target folder into which the file/folder will be saved. Once you do it, hit Ok. There you go!
Conclusion of CryptoLocker Virus Removal Guide
I hope I gave you complete information about CryptoLocker ransomware. Though I haven’t stepped much into the technical aspects, you know what it is and how to remove it, don’t you? You can also go through ODIN removal guide to know more about ransomware family!
Like they say prevention is better than cure. So, I strongly recommend you shouldn’t open attachments from strange email addresses. Moreover, approach official and reliable sources to download desktop applications.
Every time you use internet, stay alert & don’t get yourself into online traps. Stay tuned to Ransomwares.Net for more updates!

Comments are closed.